23
Aug 2021
Microsoft 365 security assessments
Independent, 3rd party security assessments are integral to understanding and validating your Microsoft Office365 security posture. These assessments may be required to prepare for a larger compliance audit, as a ‘C’ level request to validate overall IT systems health or as a baseline to see whats next.
While the assessment itself will likely reveal critical insights and yet another task list for the IT team to resolve, we can help.
LightSprocket can engage with a project scope to remediate directly, we can provide guidance to the IT team, or your team can work to resolve at the pace you choose and we can reassess at set check points. We recommend when you first run an assessment to repeat that assessment annually to empower you to show independently assessed improvements over time. Once there is maturity in the program those maybe scaled back. We typically determine maturity by mutual definition, however, a guide post is usually no critical or medium severity findings, year over year, with the IT team reacting appropriately to change as recommended by Microsoft.
When you engage LightSprocket, we do not just report the Microsoft Security Score.
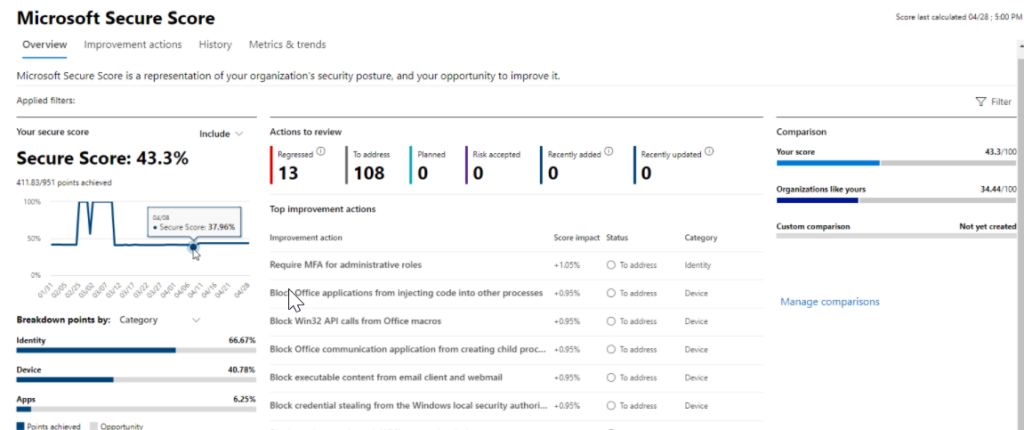
While the Secure Score can provide many wins for your organization, it can include suggestions that are not inline with your business. Our engagement spends time with the business, understanding your technology in use, how your administrators work, and where the business is heading.
One area you’ll always hear us talk about is the segregation of administrator duties away from user & mail enabled accounts. We’ll also call out email flow including Dmarc and leveraging additional parties such as Mimecast and Proofpoint, amongst others as additional levers to protect the biggest vector for our adversaries today – email phishing. Microsoft may dislike us calling it out, but we still see phishing come through their stack and we always recommend a layered defense.
In our reports you will always find the standard executive summary with a summary of our findings in Critical, Moderate, Low and Informational levels. Each finding will contain screenshots of the finding, an explanation of what the finding is, links to deeper knowledge articles, the why we think it’s its important, its severity and difficulty of resolution. We will always review the report together and you will always have the report before we meet. If we find active security issues we will immediately notify your administrators to discuss them.