06
Dec 2015
Password Expired
You ever have that one user that calls you on a trip and says, yeah i’m getting the password expired message. Of course they’re either a critical, high up person, or on a system that you know will wreak havoc if you push a new password to them. Every once in a while this happens to me.
Of course, its clearly the users fault for ignoring the 14 days of warnings before going on their trip, but you’re also not in a great position to lecture – other than your cursory poke in commentary while you’re making a few edits in the back ground since you value your job.
There’s two ways to deal with the user – hit the never expires checkbox in their AD account, and get immediately flagged by the report that runs against that flag on an hourly basis, or do a little advanced attribute edit to buy time and beg the user to change their password as soon as possible when they get back to the office.
So, lets look at how we do this.
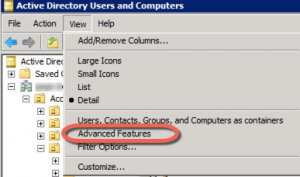
First, thing – in Active Director Users and Computers – change your view to Advanced Features, since we’re doing advanced things.
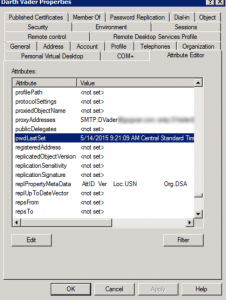
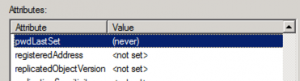
Second, look at all those pretty tabs. We want Attribute Editor. Scroll down to pwdLastSet.
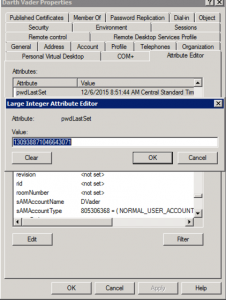
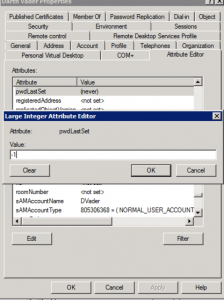
Third, give it a double click and look at that value. Ok, now that you’re read it. Make it a ‘0’, yes.. Zero.
When you hit OK, notice, that it’s now (never) as in never set. Ok, now’s not the time to panic and wonder what the heck you did to the CEO’s account.
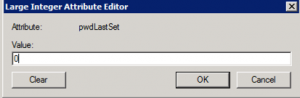
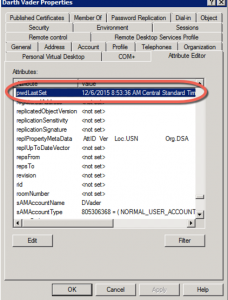
Fourth, We’re going to apply the changes, or just hit OK and close the account and reopen it. Now then, edit that pwdLastSet again, and this time make the value a ‘-1’.
Hit OK and Apply again, and take a look. Breathe.
Note – if you didn’t hit apply or ok out of the account and reopen it before applying the ‘-1’ value, you’ll get the old value back.
Now then, you’ve survived, you’re still employed and you didn’t make the Auditor’s most wanted list.
*A little general commentary is that I have tested this in my environment, and it does work safely with Office365 enabled users. I’m using Active Directory Connect to sync my accounts. As always, when in Advanced mode and in Attribute Editor, practice safe admin’ing, and if you’ve never done this before, practice on an account you can afford to lose first 🙂